In 2023, HCA Healthcare, a major hospital system in the U.S., experienced a data breach that exposed the personal information of over 11 million patients. The leaked data included appointment details, contact information, and patient service records.
A few years earlier, Anthem Inc. faced one of the largest breaches in healthcare history. Nearly 80 million records, including names, medical IDs, and employment information, were compromised.
Healthcare organizations are attractive targets for cyberattacks due to the vast amount of sensitive data they handle. Electronic medical records (EMRs), billing information, insurance details, and personal identifiers make up high-value data sets that, if exposed, can lead to identity theft, insurance fraud, and regulatory penalties.
The growing use of AI in healthcare has brought new opportunities for smarter diagnostics, predictive analytics, and operational efficiency. At the same time, it has raised the stakes for data security.
AI systems depend on large volumes of patient data to function effectively, but this data must be protected at every stage. As information flows between departments, cloud systems, and third-party tools, the risk of exposure increases.
Data masking is an AI-compatible solution for the healthcare sector that protects sensitive information without disrupting usability. By replacing accurate data with realistic but non-identifiable values, data masking ensures that patient records remain private—even if accessed by unauthorized users.
This blog explores data masking, what it is, how it works, and why it’s a crucial defense against the growing threat of a data breach in healthcare.
The Impact of Data Breach in Healthcare
Healthcare data is extremely valuable on the dark web. Unlike credit card numbers, which can be quickly canceled, personal health information (PHI) includes permanent data, full names, birthdates, Social Security numbers, insurance details, and medical histories. This information is often sold for a higher price because it can be used for identity theft, insurance fraud, and blackmail. Below are the consequences healthcare organizations face after a data breach.
Regulatory Pressure
Healthcare organizations face strict compliance requirements under the HIPAA (Health Insurance Portability and Accountability Act) regulations in the U.S. and the GDPR (General Data Protection Regulation) in the EU. These laws demand the secure handling of personal data, prompt breach notification, and proof of adequate safeguards. Non-compliance can result in heavy fines and legal challenges.
Erosion of Patient Trust
A data breach can lead to an immediate loss of patient confidence. Patients expect their health records to be private. When data is exposed, it damages the healthcare provider’s reputation and makes patients hesitant to share sensitive information in the future.
Financial Penalties
Regulatory bodies impose substantial fines on healthcare organizations for security lapses, particularly violations of the Health Insurance Portability and Accountability Act (HIPAA). The penalty structure is tiered based on the level of culpability:
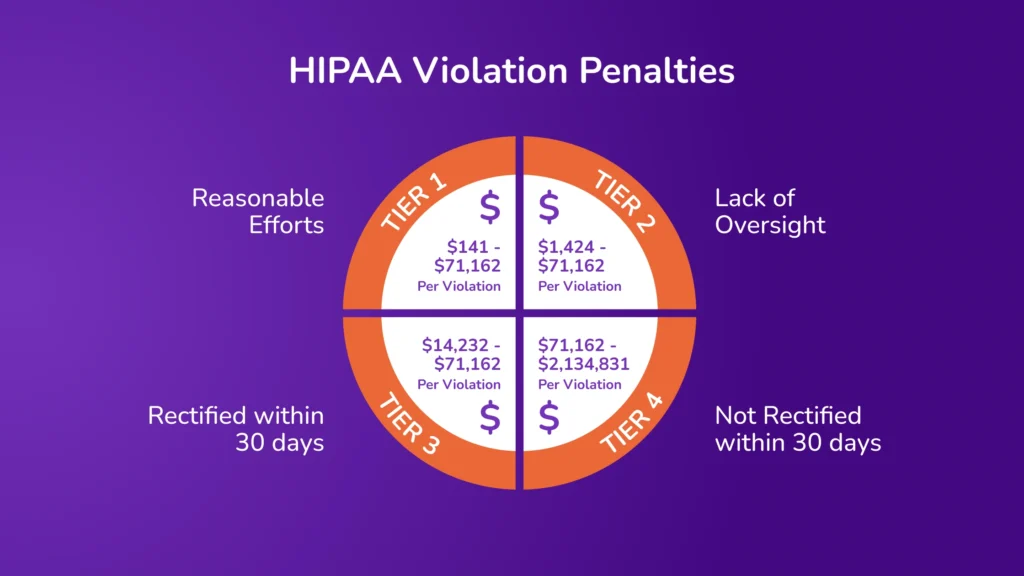
Legal Ramifications
Organizations can face lawsuits from affected patients, especially if it’s shown that proper safeguards weren’t in place. Class-action lawsuits are common, and legal battles can last years, adding to the financial and reputational toll. For instance, Anthem Inc. settled for $115 million following a breach that exposed nearly 80 million records.
Operational Downtime
Responding to a breach often involves shutting down systems, conducting forensic investigations, and restoring data backups. This can interrupt patient care, delay treatments, and strain staff resources.
The longer the downtime, the higher the risk to patient outcomes and business continuity. Ransomware attacks have led to an average of nearly 19 days of downtime for U.S. healthcare organizations, underscoring the severe operational disruptions caused by such incidents.
Data Masking: Purpose, Process, and Types

Data masking helps reduce the risk of a data breach in healthcare by replacing real patient information with realistic but fictional data, ensuring sensitive details remain protected even if unauthorized access occurs.
The main idea is to maintain the format and usability of the data so business operations and system performance remain unaffected. For example, a patient name may be replaced with a fake name, but it still looks like a name and fits into the same system.
Here is a detailed explanation of each of the types of data masking:
Static Data Masking
Static data masking is done on a copy of a database. The original data is masked once and saved in a new environment. This method is commonly used for non-production environments like development or testing, where access to accurate data isn’t necessary.
Once masked, the data doesn’t change. For example, masking data in a test environment before sharing it with third-party developers.
Dynamic Data Masking
Dynamic data masking hides sensitive data in real time without altering the data at rest. The original data remains unchanged in the database, but users see only the masked version based on their access level.
It’s often used in live environments where certain users should see limited data. For instance, a call center agent can access partial patient information while protecting the full record.
Deterministic Masking
Deterministic masking ensures that the same input always produces the same masked output. For example, “Daniel S” will always be masked as “Ray Smith.” This consistency is helpful when multiple databases need to be joined or compared. This helps maintain relationships between masked records across different systems.
Non-Deterministic Masking
Non-deterministic masking produces different results each time the same input is masked. This is more secure but can affect usability if consistent results are needed. This method helps mask data for environments where relationships between data sets are unimportant.
Format-Preserving Masking
Format-preserving masking keeps the data’s original structure and format. For example, a masked Social Security number will still follow the 9-digit format, and a phone number will still look valid.
Ensuring masked data works with systems that require data in specific formats, like EHR software or validation scripts.
Challenges in Implementing Data Masking
While replacing sensitive information with de-identified values sounds simple, implementing it brings real challenges. Here are a few challenges that healthcare organizations face while implementing it:
-
Preserving Data Usability
Masked data still needs to work. That means phone numbers must look like numbers, and medical IDs must pass system checks. If the format changes, systems may reject the data, break automated processes, or mislabel records. For instance, if a masked patient ID doesn’t match expected patterns, EHR systems might flag it as invalid, halting workflows downstream.
-
Maintaining Consistency
Healthcare organizations often use multiple databases across departments—clinical, billing, research, and support. If the same patient record is masked differently in each system, internal tools can’t reliably link data. This breaks testing, reporting, and interoperability. Consistent masking is key but difficult when systems aren’t connected or standardized.
-
Ensuring Semantic Accuracy
Masking isn’t just about hiding data; it must maintain meaning. If a birthdate is changed, age-based flags (e.g., pediatric or geriatric) need to reflect that change. Otherwise, logic built into analytics, testing, or decision-making systems might fail or generate misleading results.
-
Gender-Sensitive Data Masking
Names often reveal gender, which matters in healthcare research, treatment analytics, and compliance reporting. If names are randomly swapped during masking without preserving gender, it can distort data models. For example, a research team analyzing gender-based treatment outcomes might draw incorrect conclusions.
-
Aligning Security and Functionality
If the mask is too aggressive, the data becomes meaningless. Mask too lightly, and it’s a privacy risk. The challenge is finding the ground between protecting patient data and preserving enough detail for useful analytics, simulations, and testing.
-
Adapting to Legacy Systems
Older systems may not support modern masking tools or integrations. Healthcare providers often rely on legacy software with rigid data structures and limited flexibility. Introducing masking into these environments requires custom solutions, usually increasing implementation time and cost.
-
Performance at Scale
Applying masking to large, constantly growing datasets can slow operations, especially in real-time systems. Hospitals processing high patient volumes can’t afford delays in accessing or updating records. If not well optimized, dynamic masking can introduce latency into user-facing applications.
Real-World Applications of Data Masking in Healthcare
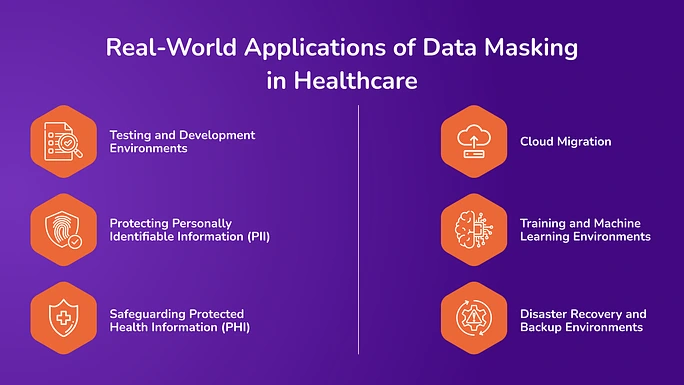
Healthcare organizations use data masking in their workflows to actively reduce the risk of a data breach in healthcare while keeping operations efficient. Here’s how data masking is used across healthcare workflows.
1. Testing and Development Environments
When developers and testers need access to patient databases for system upgrades or application development, exposing accurate data creates significant privacy risks. Data masking allows organizations to create realistic but anonymized versions of patient records. These masked datasets maintain the structure and logic of the original data, enabling accurate testing without revealing personal information.
2. Protecting Personally Identifiable Information (PII)
Healthcare systems store PII such as names, addresses, contact details, and Social Security numbers. Masking these elements before using them in non-secure environments reduces the risk of data exposure, especially when multiple teams access the same systems.
3. Safeguarding Protected Health Information (PHI)
Regulations like HIPAA require organizations to ensure that patient health data is properly secured. Data masking enables healthcare providers to share PHI for research, reporting, or analytics while protecting patient identities. It also supports compliance during audits and external collaborations.
4. Cloud Migration
As more healthcare organizations move to cloud platforms for storage and analytics, masking becomes essential. Transferring data to third-party environments increases the risk of breaches. Healthcare providers can reduce exposure without disrupting migration timelines by masking sensitive data before migration.
5. Training and Machine Learning Environments
Data is increasingly used to train machine learning models in healthcare for diagnostic tools, predictive analytics, and more. Masked data that mirrors real patient data ensures the model learns effectively without compromising privacy or breaching compliance standards.
6. Disaster Recovery and Backup Environments
Backups and disaster recovery datasets often hold complete copies of patient information. If these environments aren’t as secure as production, they become soft targets for breaches. Masking ensures these records don’t contain actual identifiers, reducing the impact of any potential leaks.
Benefits of Data Masking for Healthcare Organizations
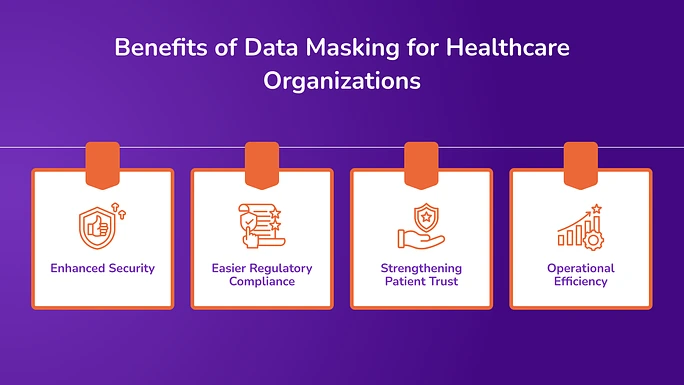
Data masking allows healthcare providers to secure sensitive information without slowing down operations. Here is a list of a few benefits of why data masking is essential for organizations:
1. Enhanced Security
Masked data can be used for development, testing, analytics, and training without risking exposure to accurate patient information. This ensures teams can work with realistic datasets while keeping protected health information (PHI) safe.
The healthcare sector saw the highest average cost per breach at $10.93 million. Data masking can significantly reduce this risk by ensuring that exposed data cannot be traced back to real individuals.
2. Easier Regulatory Compliance
Data masking helps healthcare organizations meet strict regulatory requirements like HIPAA, GDPR, and CCPA. Masked data is often considered de-identified, reducing the regulatory burden when used in non-production or research environments.
3. Strengthening Patient Trust
When patients know their data is handled securely, even beyond clinical use, they reinforce confidence in the provider. Data masking prevents misuse or accidental exposure, especially in large, distributed healthcare systems where multiple teams access data.
An Accenture survey found that 1 in 4 patients would switch providers if their data were compromised. Strong data protection measures like masking can help retain patient loyalty.
4. Operational Efficiency
Data masking enables safe data use across different workflows, such as application development, training, analytics, and cloud migration. It reduces the need for complex security barriers in environments that don’t require access to accurate data.
Healthcare organizations face growing threats to patient data every day. By using data masking, they can protect sensitive information without slowing down their work. Masking replaces real data with fake but realistic values, so even if someone gets unauthorized access, they won’t see anything useful. This helps meet privacy rules and maintains patient trust. Since a data breach in healthcare can lead to significant losses and legal trouble, using data masking is an innovative and necessary step.
Facing Data Risks in Healthcare: Why is Avahi AI the Right Platform for Data Security?
Healthcare organizations deal with large volumes of sensitive data, patient records, insurance details, diagnostics, etc. Securing this data while keeping it usable for care delivery, research, and operations is a significant challenge.
Avahi AI is a purpose-built platform that helps healthcare providers manage, protect, and work with data more efficiently. It offers a powerful Data Masker feature that is designed to make data security simple, fast, and effective. Here’s why it’s a smart choice:
1. Easy-to-Use Interface
The platform features a straightforward and intuitive layout that requires no technical background. Users can upload files in .txt, .doc, or .pdf formats and process them quickly. The setup is simple, allowing teams to start without extra training or support.
2. Fast and Accurate Masking
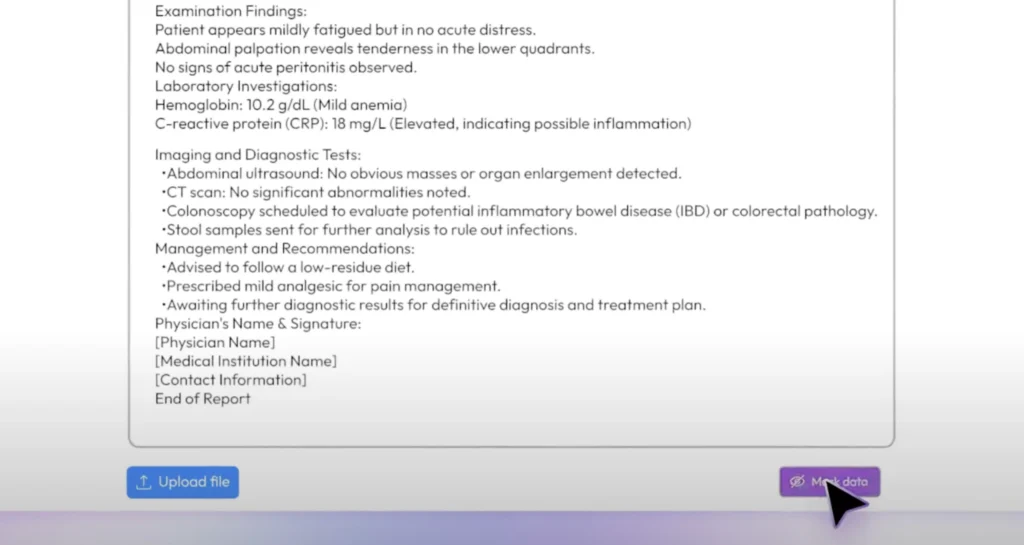
Sensitive data is quickly masked and replaced with realistic values. The tool preserves the original structure and format of the data, which is essential for testing, training, or analytics. It also maintains semantic consistency, preserving correct age ranges and gender data, making the output meaningful.
3. Summary and Side-by-Side View
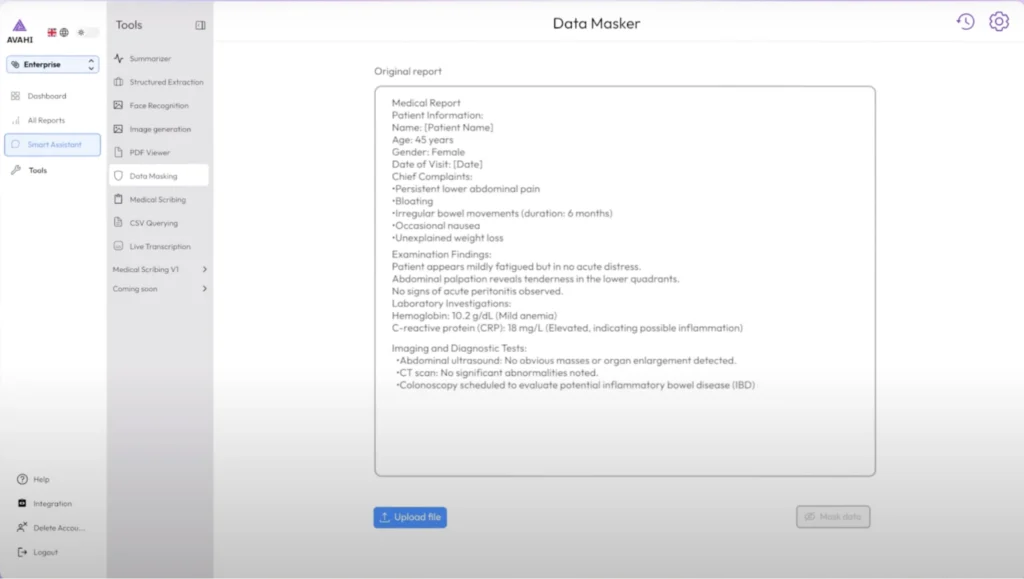
Avahi AI automatically generates summaries of masked content for quick understanding. It also allows users to view the original and masked versions side by side, making verifying results and conducting audits easier. This feature simplifies validation and cuts down on manual review time.
4. Built for Healthcare Use Cases
Avahi AI’s Data Masker is designed to handle Protected Health Information (PHI) and Personally Identifiable Information (PII). It supports key compliance standards like HIPAA, GDPR, and other data privacy laws. The tool ensures that masked data remains entirely usable in electronic health records (EHRs) and medical analytics platforms.
5. Supports Secure Workflows
Data Masker is ideal for non-production environments like development, QA, research, and training. It ensures that sensitive data is never exposed, even when shared with external teams. This helps reduce risks during cloud migration or when working with third-party vendors.
6. Saves Time and Resources
The tool reduces the time IT teams spend on manual processes by automating data sanitization. There’s no need to build custom scripts, which saves effort and resources. This allows teams to focus more on innovation and less on compliance challenges.
By choosing Avahi AI, healthcare organizations gain a reliable platform that enhances security, improves data usability, and helps meet regulatory standards, all while saving time.
Discover Avahi’s AI Platform in Action
At Avahi, we empower businesses to deploy advanced Generative AI that streamlines operations, enhances decision-making, and accelerates innovation—all with zero complexity.
As your trusted AWS Cloud Consulting Partner, we empower organizations to harness AI’s full potential while ensuring security, scalability, and compliance with industry-leading cloud solutions.
Our AI Solutions Include
- AI Adoption & Integration – Utilize Amazon Bedrock and GenAI to enhance automation and decision-making.
- Custom AI Development – Build intelligent applications tailored to your business needs.
- AI Model Optimization – Seamlessly switch between AI models with automated cost, accuracy, and performance comparisons.
- AI Automation – Automate repetitive tasks and free up time for strategic growth.
- Advanced Security & AI Governance – Ensure compliance, fraud detection, and secure model deployment.
Want to unlock the power of AI with enterprise-grade security and efficiency?
Get Started with Avahi’s AI Platform!
Schedule a Demo Call
Frequently Asked Questions
- What is data masking, and how does it protect patient information?
Data masking replaces real patient data with fake but realistic values, preserving usability while removing identifiable details. Even if masked data is accessed by unauthorized users, it can’t be traced back to individuals, making it ideal for non-production environments like testing, training, and analytics.
- Why is data masking important in healthcare compliance?
Data masking helps healthcare providers meet regulations like HIPAA and GDPR by reducing exposure to protected health information (PHI). Since masked data is considered de-identified, it’s safer to use in research or third-party systems, reducing both regulatory risk and operational friction.
- Where is data masking used in real healthcare environments?
Healthcare providers use data masking during application testing, machine learning model training, and cloud migration. It’s also applied to protect backups, development environments, and reporting workflows, ensuring sensitive data remains secure across all touchpoints.
- What challenges do healthcare organizations face with data masking?
Implementing masking isn’t always easy; it must preserve data format, maintain consistency across systems, and work within legacy software. If not done properly, masking can break workflows or distort analytics. That’s why healthcare-specific tools are essential.
- How does Avahi AI’s Data Masker help healthcare providers stay secure?
Avahi AI offers fast, format-preserving masking designed for healthcare use cases. It supports compliance, maintains data usability, and simplifies audits with side-by-side views and automated summaries. It’s built to keep PHI protected without slowing down operations.